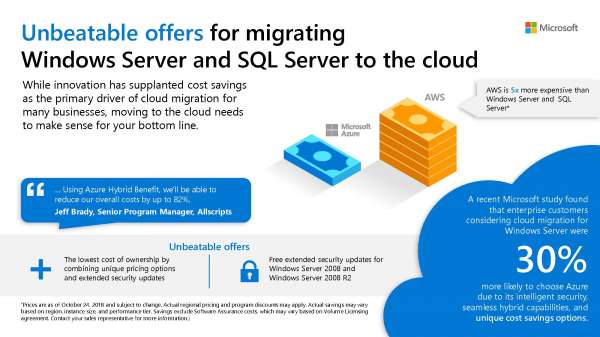
There are several reasons why a comprehensive information protection approach is so necessary. People are working in new ways. Data is being created and shared across boundaries – across a variety of devices, apps and cloud services. Compliance concerns add a layer of scrutiny to how data is being used and shared. Azure Information Protection (sometimes referred to as AIP) is a cloud-based solution that helps an organization to classify and optionally, protect its documents and emails by applying labels. Labels will be applied automatically by administrators who define rules and conditions, manually by users, or a combination where users are given recommendations.
Even with well-intentioned employees, it’s not uncommon for workers to accidentally or inadvertently share sensitive information with others that they didn’t intend to share with. 58% of users claim to own accidentally sent sensitive information to the incorrect person. Information protection capabilities in Windows ten enables business data to be separated and contained from personal information, preventing discharge to non-business locations whereas on the device.For example, policy could be defined to prevent information created in Word from being copied to a personal email account or to a social media account.
Windows Information Protection
With the rise of employee-owned devices within the enterprise, there’s conjointly an increasing risk of accidental information leak through apps and services, like email, social media, and the public cloud, which are outside of the enterprise’s control. For example, once an worker sends the most recent engineering photos from their personal email account, copies and pastes product info into a tweet, or saves an in-progress sales report to their public cloud storage.
Windows info Protection (WIP), previously known as enterprise information protection (EDP), helps to protect against this potential data leakage without otherwise interfering with the employee experience. WIP also helps to safeguard enterprise apps and information against accidental information leak on enterprise-owned devices and private devices that workers bring round work without requiring changes to your environment or other apps. Finally, another information protection technology, Azure Rights Management also works alongside WIP to extend data protection for data that leaves the device, such as when email attachments are sent from an enterprise aware version of a rights management mail client.
Bit Locker
With BitLocker*, organizations can rest assured that their sensitive information is better protected from unauthorized access—even if a device is lost or stolen—and meet regulatory and compliance requirements. BitLocker offers enterprise grade security, providing IT with the flexibility to encrypt full disks.
BitLocker to Go does the same for removeable storage devices. BitLocker Drive encryption is a information protection feature that integrates with the OS and addresses the threats of information theft or exposure from lost, stolen, or inappropriately decommissioned computers.
BitLocker provides the most protection when used with a trusted Platform Module (TPM) version 1.2 or later. The TPM is a hardware component installed in many more modern computers by the pc makers. It works with BitLocker to assist protect user data and to make sure that a pc has not been tampered with whereas the system was offline.
Microsoft BitLocker Administration and monitoring (MBAM) provides organizations with tools that build it easy to deploy and manage BitLocker-encrypted environments, —as well as provision, enforce, report compliance, and recover BitLocker-protected data if disaster strikes.